When putting together an Integrity Management Plan (IMP), we know to consider individual threats, but what about threats that interact together to increase risk? The concept of interactive threats and how to address them has perplexed many operators. There are many reasons for this confusion, such as a lack of prescriptive language in regulations, a lack of clarity in reporting the root cause for pipeline incidents, and a lack of general information concerning interactive threats.
So, what exactly is an interactive threat?
The Pipeline and Hazardous Materials Safety Administration (PHMSA) defines interactive threats as “two or more threats acting on a pipe or pipeline segment that increase the probability of failure (POF) to a level greater than the effects of the individual threats acting alone.” It is important to note, though, that two threats existing in the same location are not considered interactive by default. We know this is a little confusing, so let’s dig deeper.
As identified in the ASME B31.8S standard, there are nine primary threat conditions that fall into three separate categories:
- Time-Dependent Threats (threats tending to grow over time)
- Internal Corrosion (IC)
- External Corrosion (EC)
- Stress Corrosion Cracking (SCC)
- Resident Threats (threats that do not grow over time; instead they tend to act when influenced by another condition or failure mechanism)
- Manufacturing (MFR)
- Fabrication/Construction (CON)
- Equipment (EQ)
- Time-Independent Threats (not influenced by time)
- Incorrect Operations (IO)
- Third Party Damage (TPD)
- Third Party (TP)
- Previously Damaged Pipe (PDP)
- Vandalism (V)
- Weather Related or Outside Force (WROF)
- Earth Movement (EM)
- Heavy Rains and Floods (HRF)
- Lightning (LIGHT)
- Cold Weather (CW)
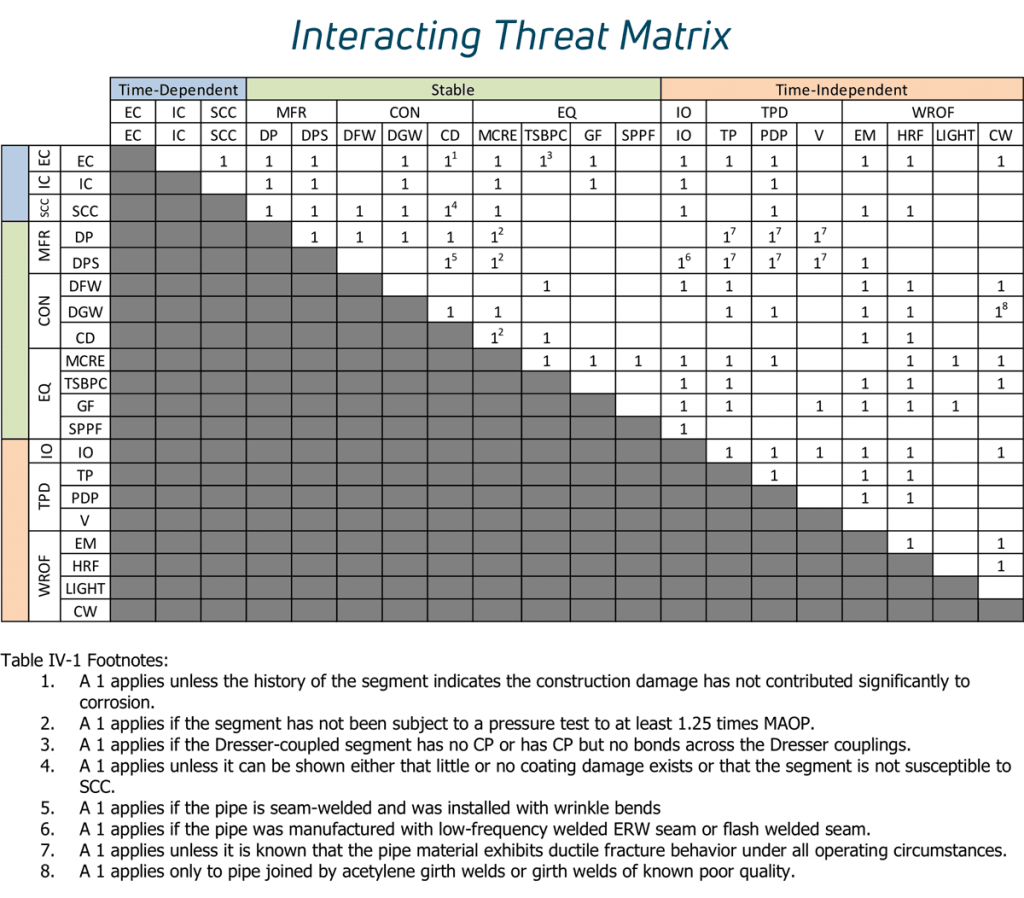
Utilizing available industry information, Eduardo Munoz and Michael J. Rosenfeld identified 98 combinations of threat types that could potentially interact in a PHMSA-sponsored study. Interacting threats are indicated by a “1” in the matrix entry for each pair of threats that interact. Footnotes to the table give conditions when the threats might interact.